WHY YOU SHOULDN'T RUN ONLY WITH AN ANTIVIRUS + FIREWALL AND WHY A PROACTIVE PROTECTION IS NECESSARY
In this first article we’ll just show that the couple scanner
(antivirus/antitrojan/antispyware) + Firewall is not sufficient to mitigate security
risks for home users.
Then we'll review and list available Desktop/Host Intrusion Prevention Systems designed for home users.
Introduction
Mr and Miss “hé we’ve bought our first PC yesterday” often consider only the
need of an antivirus, and their children Kevin and Kevina have heard vaguely of
the need of a firewall.
But if we take into consideration the evolution of internet threats (attacks and
malwares) which become more and more sophisticated; and the weaknesses of
scanners protection, we need to admit that alternative approaches such as
proactive solutions can be necessary.
Malwares and threats: more and more sophisticated
Threats and Malwares are becoming more and more sophisticated.
In the past, there was sometimes a competition between virus writers groups: which virus and worm will generate the fastest infection and which one will cause the more damage.
Threats become less noisy: if the goal is always criminal, the target is more to
steal finacial informations, and then real money, but as silent as possible.
That's why the malware terminology has evolved from basic trojans, virus and
spywares to crimewares, krugueware and so on.
Websensesecuritylabs reports each day cases of malwares and phishings attacks.
For instance here's an example of crimeware with Petrobras and Losango
An an other interesting example here.
For more information about the subject, it can be suited to take a look at these
links and papers:
Future Trends of Malwares by D.Dantchev
Viruslist (Kaspersky)
Websensesecuritylabs report2005 (pdf)
McAfee Virtual Crime Report (pdf)
Crime-research web site
Limitation of scanners in general and antivirus in particular
necessary than an AV:
if Mister Bean closes his door in his Alaska home, it’s much
more important than if his video camera alarm detects a wolf, a burn or a cat.
Without door protection and in front of a grizzly, he can begin a prayer.
The main concept of scanners is to protect a system by catching malwares with
signature database: they block only what they know.
It’s like the police which tries to combat crime only with a criminal database:
there’s a criminal database in most countries, and each day, crimes are commited.
The limits of signature database file protection is evident:
-any programmer can create his own malware for his own goal: the less his tool is
noisy, the more he has chance of success.
Since a malware is not dicovered in the wild, and reported or submitted, it can still
unknown for a long time.
-Zero hour/day malwares take advantage of vulnerabilities, and it ‘s often a great
vector for malwares, specially for trojans and worms.
And if the vulnerabilty concerns the OS, it’s much more serious: this is not the job
of AV and scanners publisher to patch the OS.
And recently, a Windows vulnerability related to WMF files has been immediately exploited as it is illustrated here or here again for bots.
Zero day malwares are really an important problem for scanners publishers: they're confronted in front of their own limits: how to prevent unknown malwares and how to increase the creation of an antidote as quickly as possible.
AV-Test.org has shown that it requires a minimum of time (Kaspersky).
There's consequently a laps of time of total insecurity: the protection does not operate in real time.
Does a bank or an online shopper addict shoul be considered as secure with only an antivirus protection?
As usual with security, the protection is never ultimate.
Some publishers integrate heuristic and proactive solutions such as Nod32 with
ThreatSence, or like Panda with TruPrevent and BitDefender (HIVE technology)
which has been higly rated by AV-Test.org for his results in recent tests; and a
few of them integrate a zero day/hour protection like VirusBuster with the
Commtouch zero hour defense technology.
An example of defense against zero hour virus is provided by Ferris Research and is explained here and available as a pdf.
Sophos and McAfee also integrate a zero hour defense with the Proofpoint technology, but only for a corporate environment.
Each publisher tries to implement new technologies to mitigate signature file
detection weaknesses, and also to stay in the right market's wagon...business is business as usual.
But is it really enough? Not sure, really not sure...
Some antivirus without signature file database like Invircible and Viguard with the
DVP use since years a proactive technologies mostly based in integrity protection.
I.S.S also includes such technologies (VPS or virus prevention without signatures)
in its products to combat new and unknown virus.
I.S.S which sells intrusion prevention (and vulnerability) system softwares
provides interesting white papers about limits of signature detection (examples:
The lifecycle of a vulnerability).
Some products combine signature file detection with proactive technologies based
in behavioral blocking such as Safe'n Sec, A2, Online Armor (keyloggers signature
database) or WinPooch/ClamAV and PrevX.
This is here certainly an interesting evolution for scanners.
In all cases, the antivirus market is higly competitive, and the rule is always the
same for any business: evolve or die.
-antivirus themselves can be affected by vulnerabilities, bugs, flaws; another
good vector for intrusions (Buffer overflows for instance) and opportunities for
malwares creations.
Here for instance a quick search on Secunia
detect new or unknown malwares: even heuristic engines are limited, and can’t
covered all malwares programming possibilities.
-malwares are becoming more and more sophisticated and use many techniques
to evade scanners engines: it can be packers like Morphine, Executor, Antidote,
rootkit tecthnologies (API hooking, memory subversion), cryptovirology and so on.
If we use API hooking with a legal software (Hide Folders XP 2) to hide a test file (or any malware) like eicar.zip, it is not detected by an antivirus like Kaspersky for instance: we can hide a collection of virus on any desktop, and scanners will detect nothing (fortunately, this tool is certainly more used to hide a collection of porn babes images from childrens, wifes or girlfriends!).
-Antivirus are mostly designed to combat malwares, and not attacks.
Phishing is statistically an attack which increase the number of victims every day.
Some antivirus softwares integrate anti-phishing protection: in fact, this protection is often limited (blocks private informations from being sent) and can't cover all techniques used in phishing like web spoofing, Cross Site Scripting...).
-even the most exhaustive malwares databases (Kaspersky for AVs and
Webroot/Sunbelt for ASs) can't take the census of ALL available malwares.
Adding new signatures files day after day is for publishers a Sisyphus and Danaides torture.
We can take a few example to show that it’s not diificult to install a keylogger, a
trojan, or a backdoor without being detecting by the majority of antivirus.
Example 1: There’s a real problem with keyloggers, simply because in a corporate
environment these softwares can used to spy employees.
We can take for instance KgSpy: during my HIPS test last year, i’ve submitted it to virus total online scan, and only Kaspersky has detected it:
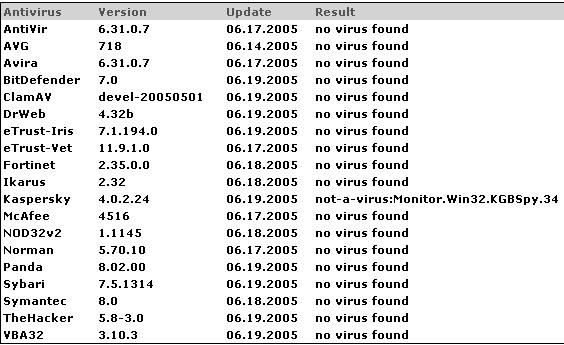
Here again the result of an online scan with this image.
Example 2: some banks provide virtual keyboard solutions to combat id account theft.
But as software is not security, this solution is not secured at all, but it costs
less money than hardware or authentication solutions (more info here).
Debasis Mohanty for instance has prooved against Citibank that their solution
was not secured, and has created a specific tool to demonstrate his POC.
So let’s scan this tool on Virus Total: result here.
Example 3 : virtual keyboard keyloggers can be downloded for free on the net,
here’s an example, mostly intended for demonstration purposes: result here.
Example 4 : now a simple experience: we use a zip file of eicar test:
the image for an online scan: nothing is detected (more info about this technique).
Example 5 : with a backdoor based ICMP (i've renamed the file): the file is not recognized, and great, anyone can use it... and not only to audit his line defense.
Example 6 : with a nice french vbs trojan: here's the scan's result (nothing is
detected).
And there’s many undetected files and methods that we can use for bypassing
scanners engines with no particular know how but just by using Google.
Andrey Boyora for instance, has studied the weaknesses of antivirus softwares.
The complete and very interesting study and research is available here ( HTML).
exploitation.
At BlackHat Europe 2005, Wheeler and Mehta from the X-Force team have also
In the past, the problem was already commented: example with the article:
"antivirus: great business, lost cause"
Why antivirus protection just isn't enough 'by ISS)
Antivirus Insecurity
Dont't Play the Blame Game
Why relying antivirus signatures simply doesn't work anymore?
The Contemporary antivirus industry and its problems (by Eugene Kaspersky)
Other Links and Resources
-antivirus independent tests (only the tests provided by the two Andreas can be
really considered as independent):
AV-Test.org
AV-Comparatives
Virus.gr
Lornet
Malware blog (test in the wild by Eric Johansen from IBM)
Overclockers
About virus and antivirus:
Wikipedia
Cknow tutorial
Claymania
Securitydocs
Stanford University
Virusall (other links on this page)
Antivirus-online
Softpanorama (exhaustive and recommended site)
And also the giant resources site of Eric Howes (virus info or antivirus products)
Online Scan
Many Antivirus publishers provide online scan on their web sites (Panda, Symantec/Norton, NA/McAfee and so on) or the possibility to scan specific files.
But this solution is quite intrusive and an interesting alternative is to use some tools like Sysclean (TrendMicro), Vcleaner (removal list) or MicroWorld Toolkit.
Virus Total
Jotti Virus Scan
Johannrain
Databases:
The Wild List
Virus Bulletin (registration required)
Online Malware ReSearch Tool (launch simultaneaously a search in many AVs database)
Antivirusprogram
Viruslist
Antivirus-online (scanners vendors)
Other interesting sites
Malwareblog
Wormblog
F-secure blog
Infectionvectors
