WINDOWS ROOTKITS COUNTERMEASURES Part 4 and End: Windows Rootkits Prevention
ROOTKITS PREVENTION MEASURES:
The more interesting method for avoiding rootkits or mitigating risks of infection is to apply prevention measures.
Most of these methods requires to use only Windows as the first line defense.
***HARDEN WINDOWS:
This step is very important for any Windows installation, not only against malwares like rootkits.
An example of checklist can be found on:
-Labmice Techtarget,
- or on Malwarehelp.org.
It can be also suited to take a look at my « Hardening Windows » section.
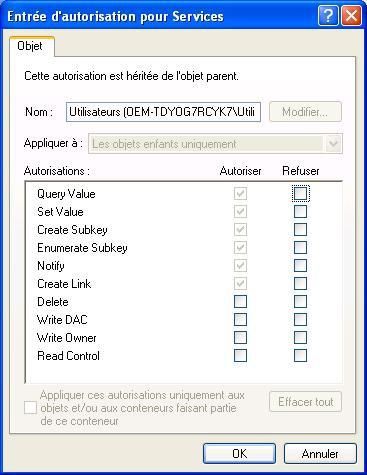
An important tweak for instance is to set up restrictive permissions for HKLMSYSTEMCurrentControlSetServices keys (or even to disable service creation by changing the value to 4).
***DEPLOY A STRONG LINE DEFENSE:
It’s really amazing but there’s many new users who surf without a firewall.
As if it’s not serious to explore Alaska with a swimsuit, it’s also not serious to explore the web without a firewall: it’s the core of any line defense.
Some examples of home users protections can be found:
-at Morgud site,
-or at Wilders Forum for questions about line defense suggestions,
-at Eric Howes pages.
As we use to be neutral and objective on this blog, we’ll only give examples of free line defense:
Firewall + malware scanner+ Personal HIPS (Host Intrusion Prevention System)+ Web Content filtering.
Jetico is currently one of the most effective free firewall available, but there’s also good alternative choices as Kerio, Sygate, Zone Alarm, and many others.
Avast, AVG, BitDefender, A2, are among good malwares scanners: the goal here is not to use them all, but to choose only one or two of them: unfortunately, no one is efficient for rootkit detection.
Free antivirus are often quite limited, and choosing a good and paid one is consequently more appropriate (a good list of AV publisher is available here).
Currently, and as far as i know, F-Secure, Kaspersky, AVZ and Sophos are the more armoured against rootkits.AVZ is a promising antivirus, but unfortunately not available yet in english.
The detection of HackerDefender via APIs can be seen here.
NB. It can be suited for paranoiacs to avoid very well known and popular products from the giants of the security business) simply because an attacker has more opporunities to bypass them (these products are often more concerned by vulnerabilities because they're popular and mostly used!).
Content filtering is often forgotten by most users.
And it’s really necessary to have a web filter installed on his system.
Malicious Mobile Code are often an infection vectors, but could also be used for gaining access to a computer.
Proxomitron is an excellent choice, even if this genius tool is more intended for experimented users.
Privoxy or WebWasher are some alternatives.
A web content filter can be used in combination with a sandbox: in this case, SandBoxie is a highly recommended product.
SandBoxie limits risks of infections and also limit’s the impact of some attacks.
If someone try to install a rookit remotely, the rootkit will not able to run.
And the result is the same if we try to install a rootkit under SandBoxie: rights and privileges under SandBoxie are limited:
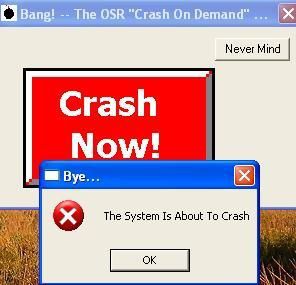
With the OSR crash utility which requires administrator privileges, we can see that the system is about to crash, but in fact, Sandboxie blocks the action.
Personal HIPS are the most important anti-rootkit defense after the firewall.
Many of them have the ability to detect service/driver installation which are often required for rootkits.
Moreover, theses Desktop IPS operate at a low level and acts as a service associated with a kernel driver.
-Samurai
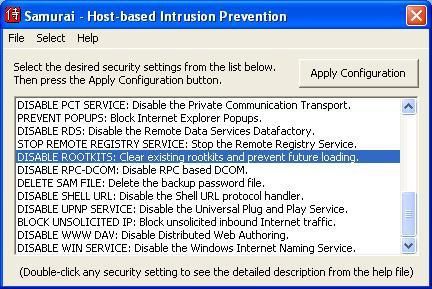
Samurai is more an hardening tool with HIPS feature than a complete desktop IPS.
It require just to enable the anti-rootkit option, and then each time that a kernel driver tries to be installed, Samurai warns the user with a popup alert:
Example with HackerDefender:
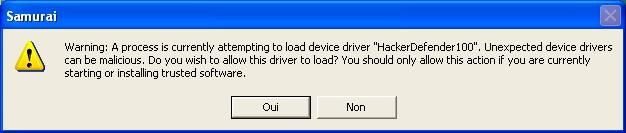
Example with FU:
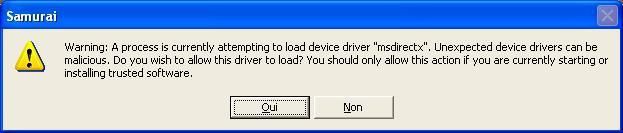
Samurai is an install it and forget it, and is a good choice for people who are not familiar with behavioral blockers and applications firawalls.
-AntiHook:
AntiHook is certainly one the most effective free desktop Intrusion Prevention System available for home users.
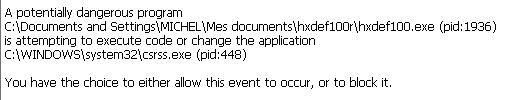
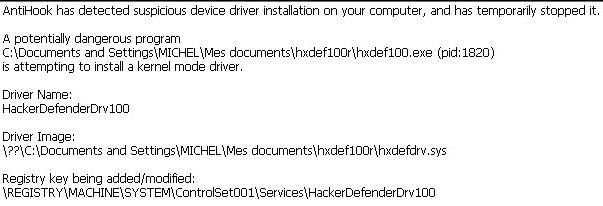
AntiHook can detect service/driver installation, but has also the ability to detect attacks intended to modify processes.
Example with HackerDefender:
Example with Fu:
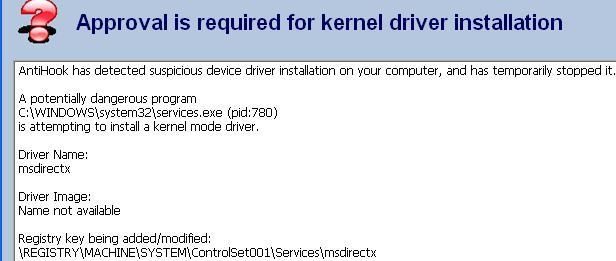
It's quite amazing to find so efficient products for free.
According to Ivo Ivanov from Infoprocess, one of its coder:
approach for API filtering to eliminate the race with Rootkits that have
been installed prior to run AntiHook by parsing the physical image of
ntoskrnl.exe. AntiHook computes the pointers to the original APIs stored
Service Descriptor Table to establish a static trusted baseline with the
operating system kernel. This technique ensures that filter functions
installed by AntiHook are called prior to original native APIs. This is a
much more effective defence and it ensures that AntiHook would “get there
first” even if a hidden rootkit is already running.
I hope this would shed some light on process hiding."
-IceSword:
IceSWORD as we’ve seen it in the previous article is more a detection tool, but it has the ability to deny process and thread creation (for advanced users).
NB. Limitations of Desktop IPS/Personal HIPS (free or paid) : as we mentioned it, desktop IPS prevent service/driver installation when they're enabled.
-if we launch the rootkit on DOS mode (only creates registry keys with the automatic service), the rootkit is not detected and neither blocked at the reboot;
-or if we install the rootkit when the Desktop IPS are disabled (case for softwares installations), nothing is detectd and blocked when we enable again the Desktop Intrusion Prevention Systems.
This remark concerns all HIPS listed here and even paid ones (ProcessGuard, Securitask 2005, System Safety Monitor and Viguard):
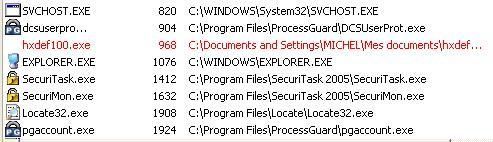
NB. Since only home users are concerned by this article, we have not mention some IDS like Samhain for instance (which uses integrity checking)..
***LOG IN and RUN as an USER:
Rights and privileges are not the same if we’re logged as an user or as an administrator.
Example if we try to run a program which requires administrator account:
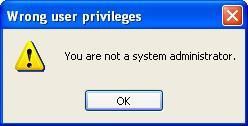
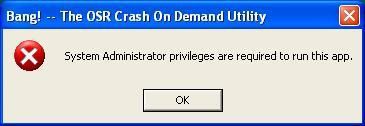
Example of rights as an administrator:
-administrator account is required to install service/driver,
- most of rootkits needs to install service/driver,
Consequently, by login and running with an user account , that will prevent rootkit installation locally and accidentally by the user, or remotely by an attacker who has gained access to the machine.
And if it's often much more difficult to gain admin. privileges than to gain only access to the target machine.
It’s only suited to log as an administrator for system's maintenance (like Windows update, service configuration) or for software installations.
Unfortunately, this solution is not always useful because some games and programs require to run as an administrator.
But there's tools and ways for using principle of least privileges with efficiency.
This" best practice" is one of the most important and effective prevention measures against rootkits.
For more information, Aaron Margosis explains on his blog why we should not run as an admin, Derek Solder provides also interesting articles about the subject, and the reader could also take a look at the part 3 of my "Hardening Window" section.
***BEST PRACTISES:
-Make regular back up of a clean image of the system:
That seems evident, bit it's sometimes needful to repeat some obviousnesses.
If a computer is infected by a rootkit, the most radical solution is to reformat the hard drive and to reinstall a clean image of the system.
If the date of the rootkit installation can be determined, then choosing the right back up will be less difficult.
If there's any doubt, a total reinstall of the original and virgin system is more recommended.
-Know what is installed on the system:
Many users like to try softwares (games, utilities, security products etc) and don’t monitor changes that which occur on their systems.
Consequently, they could have many running services, applications and loaded drivers that they ignore totally the existence.
That’s why it can be helpful to take a snapshot of the system before any installation: then we can know what service, file, driver, registry key have bee added and by which application.
Example of free monitoring softwares can be found here.
Locate32 is also a highly recommended soft: it creates a database of all hard drive files and can detect changes.
Once the rootkit is killed (service, by SVV etc), all hidden files appears clearly on the hard drive:
Device Tree is also an interesting tool for printing the list of installed device/drivers.
It's also very important to uninstall or remove any unused file, application, game or program, or it will facilitate the intruder's job when he'll need to rename his rootkit.
-Take care of infection vectors:
Most often, P2P, Relay Chat like IRC, Instant Messaging (MSN, Yahoo etc) are really a paradise for script kiddies and other attackers.
That’s why it’s often helpful to scan P2P files with a good antivirus, and to run them firstly on a virtual machine.
The user must be very cautious with all kind of social engineering attack which uses a link (via mail, IRC, MSN etc): it could be a BOT, a backdoor, a Trojan, or a rootkit: is it really necessary to click on the link?
-check the system regularly (once a week for instance).
There's tools for automatic checks (nncron is a great utility, even if the paid version is much more powerful than the free and lite version).
-never store sensitive, personal or confidential data on the hard drive, particularly for lawers, writers, scientists and any user for the one that data represents a value.
External drives, pendrives and USB memory flash exist with biometric authentication.
-Stay aware about the evolution of threats.
***LOCK the SERVICE DATABASE:
This tweak is an interesting wariness if we’re running as an administrator.
By using a Windows command line, we can lock the Service Database: in this case, no service (new or not) will be able to start.
The command is simple: "sc lock"
If we try to execute some programs which require to run as a service and load kernel driver, we’ll get some popup alerts like these ones:
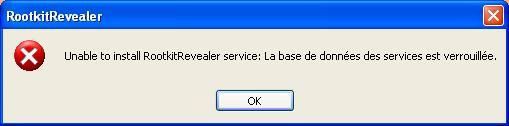
Translation: Unable to install RootkitRevealer service: the service database is locked.
If we try to install HackerDefender on a command line with this « sc lock » enabled, the service is installed but:
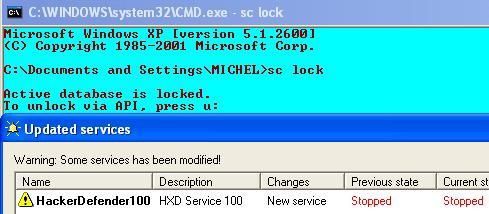
-nothing is hidden (files, service, backdoor etc),
-the rootkit is not running (executable and service).
Consequently, the event (registry entry) can be easily detected with free registry and services monitors such as RegWatcher and Winservices.
This command blocks any service (new or not) from starting, not from being installed.
***Change OS religion: Forget Windows and migrate to an alternative OS:
This idea could be quite exciting for users who are not satisfied by Windows or who want to discover other operating system.
Unfortunately for them, all OS are concerned by rootkits.
In Unix systems, the problem is well known since twenty years: if an user has Linux1 installed, he would be confronted to possible infection by Adore, Torn, Knarck or SuckIT rootkits.
Mac OS is certainly less attacked because less utilized, but the Mac world has also its rootkit threat and insecurity2.
FreeBSD is certainly one of the most secure system, especially considering its more secure kernel level.
An interesting idea is to have two OS installed on the same hard drive.
This is simply possible with virtualization softwares such as VmWare (a good article about the subject can be readen on CastleCops site, and more info on this dedicated blog), but it's diffcult to assure this solution.
It depends on many criteria: if Windows and Linux are installed for instance, then Linux will not be afected by Windows rootkits.
Moreover, if the intruder has hidden an administrator account, then he could probably infect the other OS (Linux in our example) with appropriate rootkits (Adore, Knarck).
A more simple solution is a migration to Vista: with Windows Defender, and perhaps the released of Strider Ghost Buster and other features (like account management), Windows will certainly be more armoured against stealth codes in general and rootkit in particular.
***PAID PRODUCTS FOR PREVENTION:
-Personal HIPS:
ProcessGuard and SecuriTask 2005:
These products have the ability to block service/driver installation simply by checking a box option.

ProcessGuard is more powerful and effective because it blocks also the access to physical memory, access which is often needed for rootkits.
The primary disadvantage of these HIPS (with the remark above) is that they must be disabled for softwares installation; and in this case, risks of rootkit infection are real.
But they're useful for people who use to run with administrator account
System Safety Monitor:
This Desktop Intrusion system has anti-rootkits features, because it detects access to physical memory, and service/drivers installation.
Mostly intended for advanced users, it requires specific rules for an effective prevention.
Viguard:
This product does not have specific features against rootkits, but as it protects systems processes (memory), it prevents most of rookits installations.
The user can also establish specific rules to prevent them (deny creation of any new file is the more easy rule).
As far as i know, specific rootkit defense will be implemented in the future.
Safe'n'Sec:
This russian product updated recently has no particular protection against rootkits, but can easily detect suspect activities launched by rootkits:
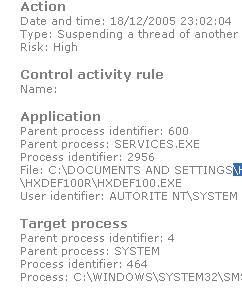
RegDefend and RegRun:
These registry protectors have the ability to detect and to prevent creation of new registry keys.
Both are able to detect and to prevent service/driver installation:
Example with RegRun at Wilders Forum.
Example with RegDefend (against HxDef and FU):
Rule without user's interaction (the creation of the keys is automatically blocked)
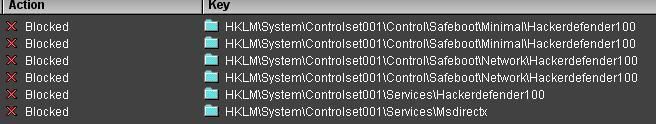
With user's interaction (the user is warned by a pop up):
Example with HackerDefender
NB. RegDatXP seems also an effective registry protector, but since the trial version has only limited features, I can’t confirm its anti-rootkit efficiency.
***Hard drive protection:
Theses solution are mostly intended to secure public computers (internet cafes, public libraries, university), but may also be deployed on home users windows systems.
When the hard drive protection is enabled, all that is written on the local disk is automatically vanished at the reboot: system's configuration, virus, spyware, and also rootkits.
They can’t prevent malwares and in our case rootkit installation, they just prevent the rootkit from being permanent.
If the attacker has find a door to gain access to the target computer (unpatched vulnerability, zero day exploit, hole in the line defense etc), he could reinstall the rootkit each time he wants (since the target host is alive).
On the other hand, any rootkit (public or paid) will be vanished after the reboot.
Therefore, this kind of protection is really one of the most interesting to keep the hard drive as clean as possible, and could be used as a real-time and permanent back up.
Well known products are provided by:
- Faronics (DeepFreeze),
- Centurion Technologies (CenturionGuard, DriveShield),
- HorizonDataSys (Drive Vaccine, based on Centurion technology),
- ShadowStore (Shadow User),
-F.G.C ( Fortres and CleanSlate)...
A short overview of this kind of products can be found on this page.
***LIMITATION OF ROOTKIT PREVENTION:
As there’s no 100% secure system, and since Microsoft keeps its architecture, there will always be a way to bypass detections and prevention measures.
Zero Day is now a business: each one can spend his week-end to find vulnerabilities, and if this one concerns Microsoft products, he can sell his discovery for socities like IDEFENSE, and then spend good time at Las VEGAS, Monte Carlo or Marbella.
We have shown that running with a limited account can prevent rootkit installation, but is it really sure?
Privileges escalation are always possible (shatter attack is a well known example) as it was shown this year with Winlogon or RunAs.
There’s also many other attacks like kernel and device drivers exploits or buffer overflow which can be used to gain access on a computer and then install a rootkit.
Moreover, it's important to remember that once the attacker has gained access to our computer, it's not our machine anymore!
From this point, all is theorically possible: the deactivation of installed security softwares (antivirus, HIPS, firewall), the access to administrator rights and so on.
Fortunately for home users, these kinds of attacks are not for script kiddies, but are often the attribute of advanced attackers who are much more interested in corporate web servers.
CONCLUSION
In this article we have introduced the rootkit threat and shown that solutions (free or paid) are available to combat them.
Rootkits are in vogue on Windows systems since one or two years, but as often, we're only afraid of what we don't know.
Generally, attacks (DDOS, Buffer Overflow...) are much more difficult to avoid and prevent than simple malwares; and as sophisticated as it could be, a rootkit is only a malware (trojan).
There's no need to deploy an anti-rootkit arsenal: the user just needs to apply simple rules on his perimeter defense: hardening his system, installing a strong line defense (firewall+ antivirus+ Desktop IPS) and making use of best practices as often as possible (surf under a non-administrator account, mitigate risks of infection...).
Hardwares and softwares products are not all, the human factor is also very important: Knowledge is power, and keys are often inside.
If a strong line defense and best practises are often sufficient against rootkits and other malwares, more important is the user awareness.
The scandalous Sony rootkit's affair just demonstrates that rootkits technologies and stealth softwares will be more and more used in the wild.
That's a good reason to keep our minds vigilants...
ACKNOWLEDGEMENTS:
Thanks to Ivo Ivanov (Infoprocess) for his answer about hooking, and to Illya Rabinovich (SoftSphere) for his first comments about this article and for the info about AVZ.
