ABUSE SHIELD
AbuseShield
" Globesoft AbuseShield" is a comprehensive tool for monitoring and controlling your desktop or server environments so that only the software you specify can run.
AbuseShield also monitor file system activities.This means that even if you, by misstake, allow a mallicious program to run, you can still see afterwards what damage the program has done to your file system."
During the installation, AbuseShield records all hard disk files and creates checksums and default rules: all running processes are considered as safe and integrated on a white list of allowed/permited applications.
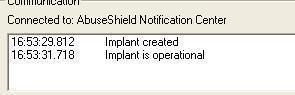
AbuseShield is a Desktop Intrusion Prevention System designed to prevent unauthauised applications from running and causing damage in a host.
This program from the suedish society GlobeSoft is paid and costs about 20 dollars.
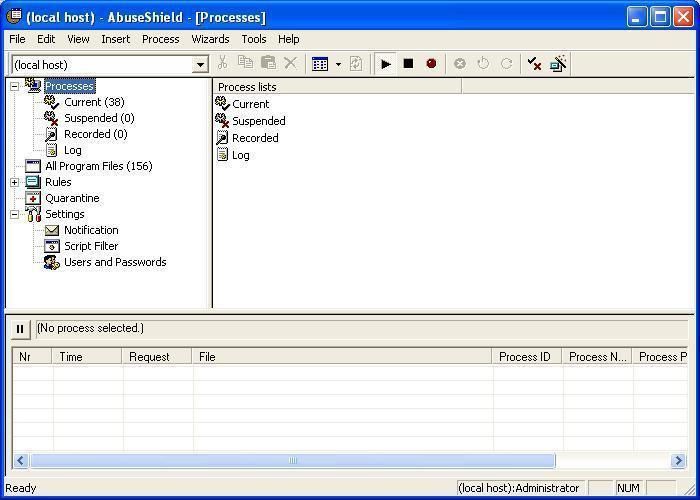
Configuration: with default rules.
***AbuseSheild is the winner against:
-Execution protection with Leaktests:
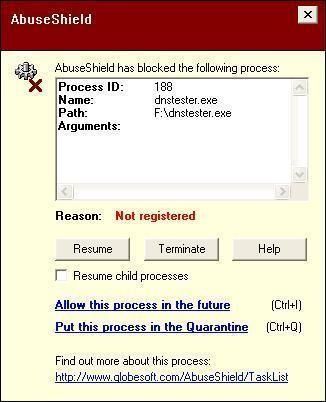
-Process Termination: in fact the process is easily terminated (the service too), but when we launch the program again, it detects that it has been terminated in a suspect way, and suggests the user to check the system again.
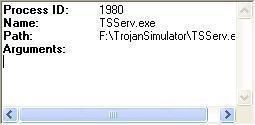
-Simulating a trojan installation with Trojan Simulator:
-CDRom autorun:
-Joke test
***AbuseShield failed against:
-Registry tests:
-with Regtest 1 and 2:
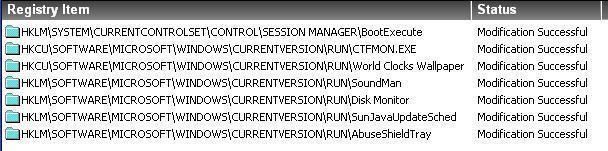
-with Scroundrel Simulator:
-dll injection:
-process hijacking:
-Finjan Tests:
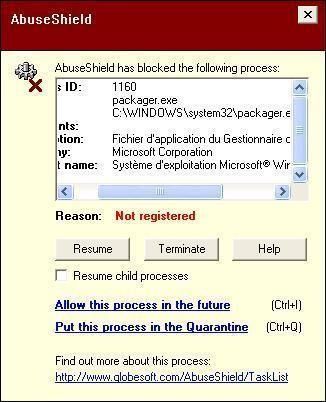
-API Manipulation:
-a-with APISpy32
-b-with Executehook
-c-with Kapimon
-Memory Manipulation:
-a-with UH:
-b-with Physmem.
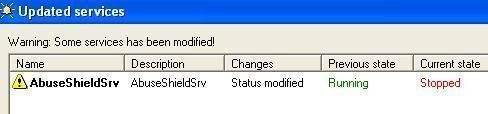
-Service Manipulatation:
-a-Service termination:
-b-driver modification: not possible:
-c-loading a driver.
-Data Theft with Trojan Demo:
-Buffer/heap overflow test
-Deactivation methods:
-a-trashcan
-b-blacklisting
CONCLUSION:
the pros:
-effective as an application firewall (the action/event is suspended/blocked since the user/administrator does not allow it),
-easy to manage and configure (type of rules such as "current, allow, system, possibility to block automatically startup entries and new applications for reducing the number of alerts and so on),
-acts as a service,
-exhaustive features and options (quarantine, central management for multiple hosts, launch the browser and query a Google search informations for a process, script filtring/blocking, checksums, snooze option for disabling temporarly the program, email notifications, certification rules...),
-efficiency of alerts: one click-one second for allowing or blocking an application, with the possibility to add the file into quarantine if the user is not sure,
-can be used by classical users and also experienced ones,
-not expensive (20 euros/dollars) (...)
The Cons:
-limited protection: monitors only execution activities (processes), not loaded dlls or sys files and registry (except start up entries),
-only available in english,
-does not protect against advanced malwares (which uses dll injection for instance),
COMMENTS:
AbuseShield is an interesting Desktop IPS for preventing unknown applications from running: any unknown or new process is automatically blocked and the user is instantaneously warned by a clear popup alert.
Easy to use, to mange and to configure, AbuseShield is certainly a good choice for beginners and classical users who wish to become familiar with such products.
This product is efficient for blocking events related to an application, but on the other hand, the protection is limited: some files (dll, sys ) and system's areas like the registry are not covered.
Consequently, this Desktop IPS is not a revolution (in relation to other ones), but appears as quite classical.
And if we consider that malwares are more and more sophisticated, AbuseShield could not be sufficient against the new generation of threats.
In this case, AbuseShield cannot be recommended in a risky surf environment, and appears more suited on family LAN managed by an administrator.
COMMENTAIRES:
AbuseShield est un produit suédois qui n'a hélas rien de bien révolutionnaire.
Si la protéction des exécutables est efficace, ce n'est pas le cas des autres fichiers (type driver ou modules).
La protection de l'intégrité du système s'avére incomplete si l'on tient compte de certains spywares utilisant des techniques d'injection de dll par exemple.
Toutefois le prix abordable (20 euros environ) et la faculté d'être utilisé de manière centralisée sur plusieurs postes peut en faire un outil intéressant sur un réseau local familial.
RATING: 7/10
